Privacy-As-Code: Preventing Facebook’s $5B violation using Fides Open-Source
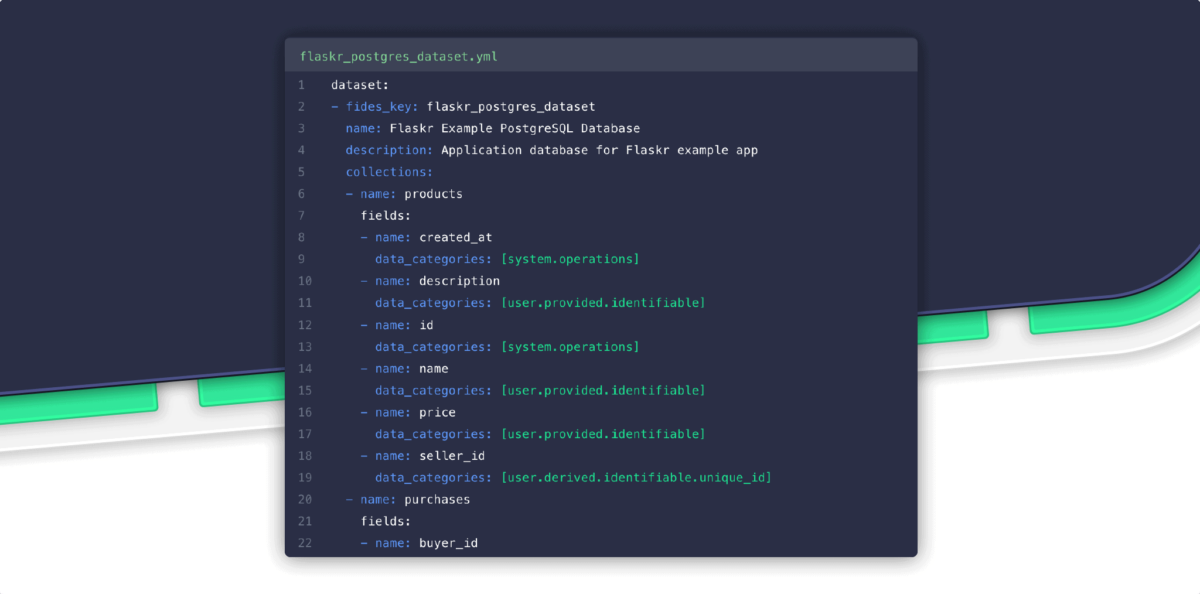
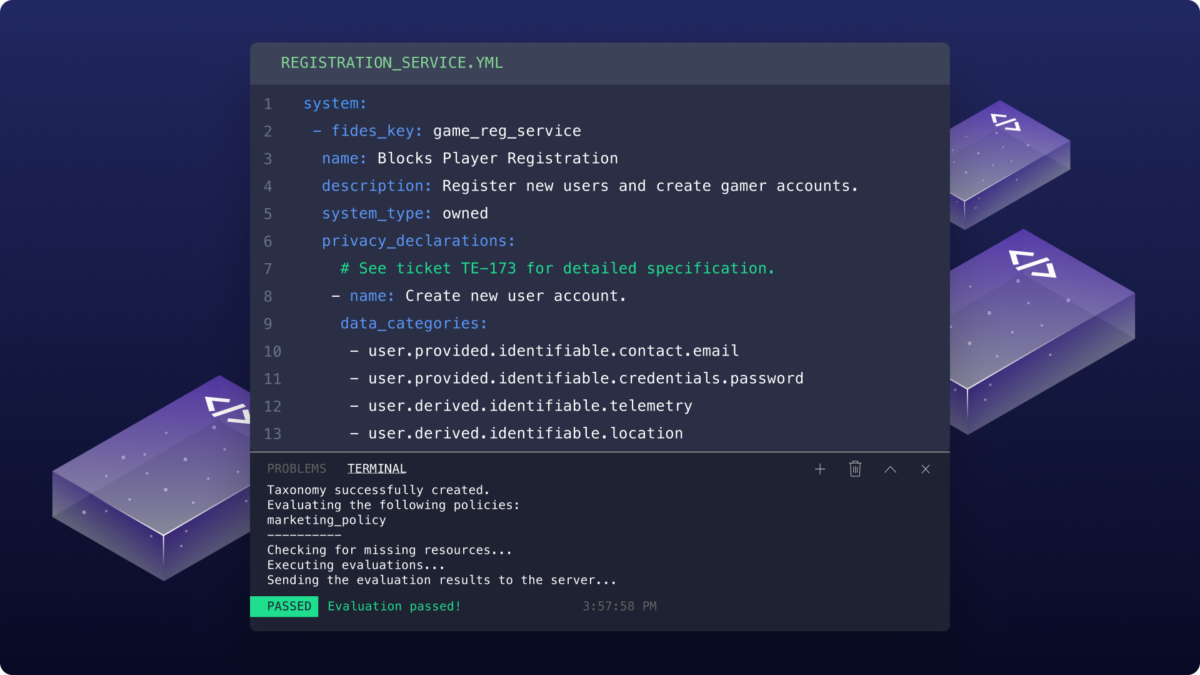
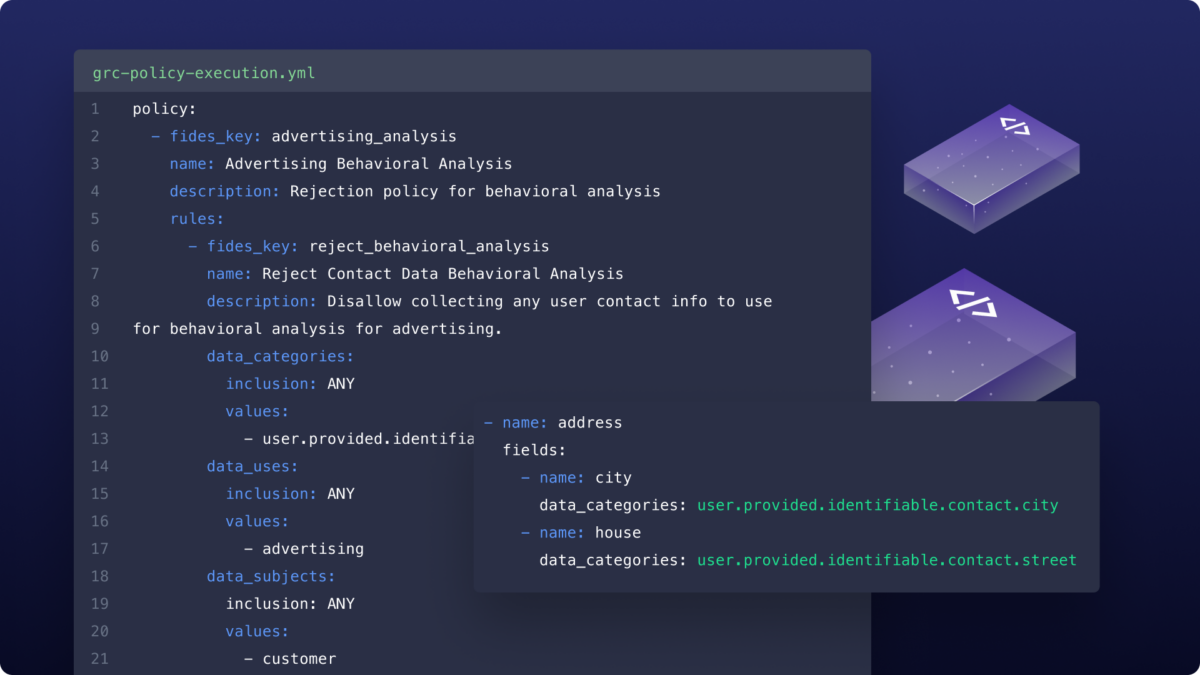
In this article, we’ll use open-source privacy engineering tools to code a policy that prohibits applications from sharing data with third-parties. This was the data governance issue at stake in a 2019 ruling by the FTC against Facebook that resulted in a hefty fine.